Intercepting Mobile Apps Over Mobile Data with Burp Suite
The Challenge of Mobile Data
When a mobile device uses mobile data, it operates on a different network than a Burp Suite setup, preventing standard proxy configurations from functioning. To bridge this gap, an internet-accessible tunnel must be established, allowing the device to reach the proxy remotely.

Step-by-Step Guide to Intercept Android Traffic
Step 1: Set Up Burp Suite
Launch Burp Suite
- Open Burp Suite on your machine. Ensure the proxy listener is active at
127.0.0.1:8080.Confirm it is running under Proxy > Options.

Establish an Ngrok Tunnel
- Download and install Ngrok from the official Ngrok website.
- Authenticate your Ngrok installation using your auth token by running:
ngrok config add-authtoken XXX- Create a TCP tunnel linked to your Burp Suite’s local proxy:
ngrok tcp 8080
- Note down the generated endpoint URL provided by Ngrok
Step 2: Configure Your Android Device
Install a Proxy Application
- Download a proxy management app such as Super Proxy from the Play Store.
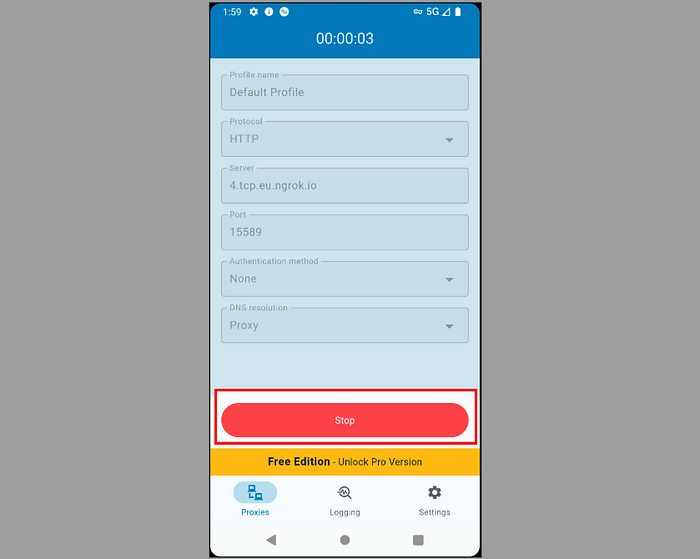
Configure Proxy Settings
- Open your proxy application and create a new proxy profile with these settings:

Parameter Value Type HTTP Host Your Ngrok hostname & Port Your Ngrok port
- Activate this proxy profile while connected via cellular data.
Install the CA Certificate (For HTTPS Inspection)
- To intercept HTTPS traffic, install Burp Suite’s CA certificate on your Android device. The process varies based on your Android version and device manufacturer.
- Typically, download the certificate by navigating to
http://burpwhile connected through the proxy and install it as a trusted certificate on root of your device.

Step 3: Test and Verify the Setup
- Open Burp Suite and go to the HTTP History tab.
- Generate network traffic on your Android device by using apps or browsing the web.
- If the traffic appears in Burp Suite, your configuration is successful.

Alternative Solutions for Private or Internal Projects
For situations where Ngrok isn’t ideal (e.g., internal corporate environments), you can self-host solutions or set up your own VPN using OpenVPN or WireGuard for secure and controlled traffic interception.
And that’s a wrap — until next time, keep exploring, keep learning!

