Understanding and Exploiting NFC Intents in Android Applications

This guide will help you understand NFC basics clearly, covering how Android processes NFC intents and demonstrating step-by-step techniques to exploit two common NFC-related security issues in Android apps
Understanding NFC: The Technology Behind the Tap
Near Field Communication (NFC) is a short-range wireless technology that allows two devices to communicate within very close distances — usually around 4 centimeters — without needing pairing or setup like Bluetooth or Wi-Fi. It’s widely used for contactless payments, public transport tickets, access control systems, and quickly sharing data between smartphones or NFC-enabled devices simply by tapping them together.

How NFC Actually Works
NFC technology relies on electromagnetic induction between two devices. First, your phone (active device) generates a magnetic field. This field then powers up an NFC tag or card (passive device) placed nearby. Once powered, the tag sends data back to your phone, which then processes this information and performs the required action.

NFC Tag Types
NFC tags are available in different standardized formats, each suitable for specific uses. Type 1 & 2 (ISO 14443A) tags are most common and cost-effective, often used for general tasks like storing URLs or contact details. Type 3 (Sony FeliCa) tags offer higher storage but are pricier, typically used for public transport or payments. Type 4 (ISO 14443A/B) tags are versatile and secure, ideal for authentication and smart-card applications. Type 5 (ISO 15693) tags support a longer reading distance (up to 10cm), useful in inventory management or access control systems. Most NFC tags, including Type 1 & 2, are rewritable, allowing you to repeatedly update or modify stored data. In this article, I’m specifically using ISO 14443A tag, as shown below.

Handling Non-NFC Devices and Disabled NFC
If your device doesn’t support NFC, you’ll see an error like “NFC not supported on this device.”

Similarly, if NFC is turned off, the app will prompt you to enable it:
“NFC is disabled. Please enable it in Settings → NFC.”

To avoid errors, ensure your device supports NFC and that it’s enabled before testing.
Writing to NFC Tags:
To create your own custom NFC tags, you’ll need an Android phone with NFC support, blank rewritable NFC tags, and the “NFC Tools” app, which you can easily download from the Google Play Store.

NFC Tools allows you to read existing NFC tags, write different types of data (like URLs, plain text, or custom information), and even format or lock tags. Writing data is straightforward: just open NFC Tools, select “Write”, pick your desired data type (URL, text, etc.), tap on “Write”, and finally, hold the NFC tag near your phone to complete the process.
How Android Processes NFC Tags
When your Android phone detects an NFC tag, it follows this sequence:
Phone detects NFC tag → OS reads the tag’s data format → creates an Intent containing this data → searches for an app that can handle this Intent → launches the matched app and passes the data.
This Intent-based handling can expose the system to security vulnerabilities, as attackers might exploit malicious NFC tags to trigger unintended actions.
The Android Manifest Connection
For an app to receive NFC data, it needs specific declarations in its AndroidManifest.xml file:
<uses-permission android:name="android.permission.NFC" />
<uses-feature android:name="android.hardware.nfc" android:required="false" />activity android:name=".MyNfcActivity">
<intent-filter>
<action android:name="android.nfc.action.NDEF_DISCOVERED"/>
<category android:name="android.intent.category.DEFAULT"/>
<data android:scheme="https" android:host="example.com" />
</intent-filter>
</activity>Android supports three main NFC intent actions:
- NDEF_DISCOVERED: For properly formatted NDEF data (most common)
- TECH_DISCOVERED: When the tag technology is recognized but not the data format
- TAG_DISCOVERED: Last resort when nothing else matches
The NFC Infiltrator App:
To demonstrate real NFC vulnerabilities, I’ve developed an Android application called “NFC Infiltrator”, which includes two intentionally vulnerable components. You can download the app directly from its GitHub repository.
Challenges Included:
- Challenge 1: Exploiting Improper URI Scheme Validation (Secured Facility)
This challenge demonstrates weaknesses in how the app handles URI schemes. - Challenge 2: Bypassing MIME Type Payload Validation
In this challenge, you’ll explore flaws in MIME type handling.
Note: Some images might look blurred due to resolution changes
Challenge 1: Exploiting URI Scheme Validation
Here’s how Challenge 1 is configured in the app’s manifest:
<activity android:name=".Challenge1Activity">
<intent-filter>
<action android:name="android.nfc.action.NDEF_DISCOVERED"/>
<category android:name="android.intent.category.DEFAULT"/>
<data android:scheme="nfcinfiltrator" />
</intent-filter>
</activity>This tells Android: “Launch Challenge1Activity when an NFC tag with a URI starting with ‘nfcinfiltrator://’ is detected.”
The Vulnerability
Let’s look at the security check in the app’s code:
public static boolean verifyCh1(String uri) {
return uri != null &&
uri.startsWith("nfcinfiltrator://") &&
uri.contains("admin");
}The code only checks if:
- The URI is not null
- It starts with “nfcinfiltrator://”
- It contains the string “admin” anywhere
That third check is dangerously loose! The string “admin” could appear: As a parameter name/value
Exploitation Step-by-Step
Let’s create an NFC tag to exploit this:
- Open NFC Tools and select “Write”

2. Choose “Add Record” → “Custom URL/URI”
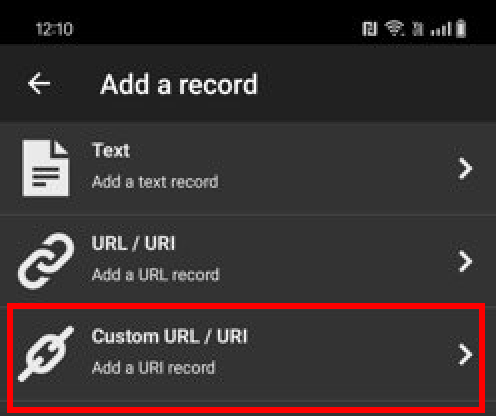
3. Enter this crafted URI:
nfcinfiltrator://access?user=admin
4. Tap “OK” and “Write”, then hold a blank tag to your phone, and the data will be written onto the tag.
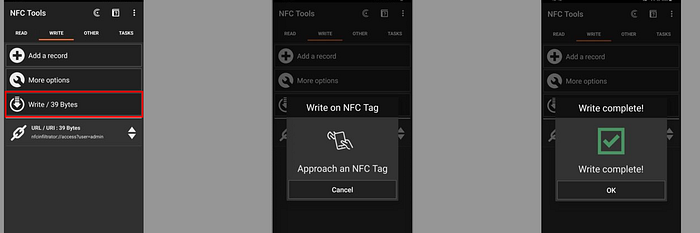
5. Open the app on an NFC-enabled device.

6. Then, open Challenge 1, and it will listen for a tag.
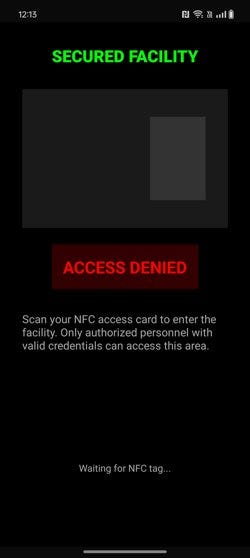
7. Tap the NFC tag, and the challenge will be solved.

What Happens:
The device reads the NFC tag and extracts the URI from it. Android creates an Intent and routes it to Challenge1Activity. The app checks if the URI contains the keyword “admin” — which it does — but it only verifies the presence of the keyword, not its correct position or context. As a result, access is improperly granted, and the app reveals the hidden flag.
Challenge 2: MIME Type Payload Exploitation
Let’s look at the second challenge:
<activity android:name=".Challenge2Activity">
<intent-filter>
<action android:name="android.nfc.action.NDEF_DISCOVERED"/>
<category android:name="android.intent.category.DEFAULT"/>
<data android:mimeType="application/x-facility-clearance" />
</intent-filter>
</activity>This launches Challenge2Activity when an NFC tag with MIME type “application/x-facility-clearance” is detected.
The Vulnerability
Here’s the validation code:
public static boolean verifyCh2(String payload) {
return payload != null && payload.contains("AUTHORIZATION_USER:CYBERSANDEEP");
}Again, the same pattern:
- Check if the payload is not null
- Check if it contains a specific string anywhere
It doesn’t validate structure, format, or context of the authorization data.
Exploitation Step-by-Step
Let’s create another tag:
- Open NFC Tools

2. Select “Add Record” → “Data”

3. Set “Content-type” to: application/x-facility-clearanceFor “Data” enter:AUTHORIZATION_USER:CYBERSANDEEP

4. Tap “OK” and “Write”, then hold a blank tag to your phone

5. Open the app on an NFC-enabled device. Then, open Challenge 2, and it will listen for a tag.

6. Tap the NFC tag, and the challenge will be solved.

What Happens:
The device extracts the tag’s MIME type and payload. Android then routes this information to Challenge2Activity. The app checks for an authorization string within the payload, finds it, and improperly grants access due to inadequate validation. As a result, the second flag is revealed.
And that’s how you can exploit NFC intents by understanding their internal flows and validation weaknesses. I hope this provided you with a clear, practical overview of NFC security basics and real-world attack scenarios.
Have you discovered other interesting NFC vulnerabilities or have experiences you’d like to share? Drop your thoughts in the comments below! Also, feel free to request any modifications or ask for more insights.
Until next time, stay curious and keep exploring!